Paul Dvorak / Editor
Want to see scary stuff? Montior hackers trying to get to the controls for an electrical substation. They are looking for weak spots probably for later exploitation. At some time, say experts, the attach will come. Fortunately, there are cyber cops with suggestions for preventive measure that may thwart the intruders.
Shortly after midnight on a near moonless morning in April 2013, several gunmen opened fire with AK-47s on the transformers at the Metcalf Transmission Substation in California. More than 100 rounds punched holes in 17 transformers, spilling over 50,000 gallons of transformer oil and shutting the station down. In 19 minutes, the gunmen caused over $15 million in damages. But rest easy, says the FBI, because the Bureau does not think the attack was the work of terrorists. The gunfire was just one volley in a battle that has already commenced. Later attacks will be more subtle than those with Russian assault rifles. They will come over the Internet.
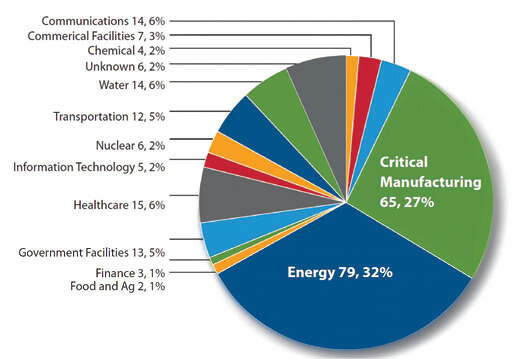
In Fiscal Year 2014, ICS-CERT received and responded to 245 incidents reported by asset owners and industry partners. The Energy Sector led all others again in 2014 with the most reported incidents. ICS-CERT says its continuing partnership with the Energy Sector provides opportunities to share information and collaborate on incident response efforts. Also noteworthy in 2014, says ICS-CERT, were the incidents reported by the Critical Manufacturing Sector, some of which were from control systems equipment manufacturers. The ICS vendor community may be a target for sophisticated threat actors for a variety of reasons, including economic espionage and reconnaissance. Of the total number of incidents reported to ICS-CERT, roughly 55% percent involved advanced persistent threats (APT) or sophisticated actors. Other actor types included hacktivists, insider threats, and criminals. In many cases, the threat actors were unknown due to a lack of attributional data.
This article can only scratch the surface of the cyber security problem because of its fluidity. However, a few of the big successful hacks have made headlines, such as the hack at department store Target stealing credit card numbers, and into the Federal Government computers, pilfering sensitive personal information from four-million government employees that can easily be used for blackmail. More intrusions go unreported by the news. Fortunately, wind farms do not seem on the receiving end of concerted attention, although experts say that anything on the web is a target.
A lot of bad people are anxious to make bad things happen to this country and its infrastructure. Foreign agents have been poking around at least several western wind farms and other unacknowledged utilities as well. It’s difficult to tell where they come from because they use many ways to mask that information, but most indications are Russia and China. The intruders are probably looking for weak spots in an overall system, ideally a way to hobble a large part of the U.S. economy, and all without firing a shot.
The problem at large
Hackers, as good a name as any for these intruders, are looking for anything they can disrupt, but specifically information on the electric grid, how to collect that information, and how to use it. “The concern is that systems on the grid are interconnected so even a small wind farm can be an entry point to systems that controls larger portions of the grid,” says Joseph Doetzl, head of cyber security for the Product Group Enterprise software within ABB in the U.S.

Turbine OEM suggests security modules to protect wind turbines
Siemens says its security concept for wind-turbines offers reliable protection against cyber criminality, a real threat for networked wind-power plants. The security modules of its Scalance S family are said to be easy to use and provide protection in a flexible, reaction-free, and protocol-independent manner. This allows securing existing networks without need to reconfigure network stations or to change the network topology.
The modules are for use in automation technology and are said to seamlessly connect to the security structures of office and IT environments. Through a combination of security measures, such as firewalls and VPN via IPsec tunnels, Scalance S protects individual wind turbines and entire wind farms against threats such as data espionage and manipulation, unauthorized access, and automated break-in attempts.
Doetzl says he is not aware of any success by hackers or first-hand accounts of widespread disruptions in the U.S. “Taking a single 100-MW wind farm offline is probably not something that would disrupt a grid or damage equipment, although there would be a financial impact. The grid, at large, does a good job of handling loads that come on and off line. Protection mechanisms are built in. The concern is that the control systems for a single generating facility are communicating with control systems for larger areas. A control system at a generating facility improperly secured could serve as an access point for another facility that has a larger impact,” says Doetzl. In security parlance, the bad guys could swim upstream.
One scenario is that hackers would simultaneously hit several plants to take as much off line as possible. “Large portions of the grid in North America would go off line along with physical damage to equipment that takes a long time to replace. A series of cascading catastrophic effects would follow, such as no electricity, clean water, or transportation,” says Doetzl.
To consider the consequences of an attack, just look back to several quite unintentional blackouts that have occurred since 9/11. The most significant one in August 2003 left northern Ohio and parts of Michigan, Pennsylvania, and New York, even parts of Canada in the dark for several hours to two days. That was an accident. Imagine someone trying to make mischief.
Fortunately, says Doetzl, Federal Energy Regulatory Commission (FERC) through North American Energy Reliability Corp. (NERC) has created mandatory and enforceable site security standards for the electric grid. “All of those have come into existence with the Energy Policy Act of 2005, with the first standards effective in 2008. New standards next year will include greater portions of the bulk electric system to address cyber and physical security for electric system facilities. The Departments of Energy and Homeland security are also publishing guidance to assist with securing critical infrastructure,” he adds.
Generally speaking, there are two aspects to the topic of cyber security. “As an owner operator, you are concerned with system availability, and that it is not damaged. So a risk analysis is involved in making sure you are taking prudent steps. For instance, it is possible to secure the perimeter of a nuclear facility and everyone that can access the critical operations within the plant. A typical wind farm, however, has many fewer employees on site and it’s typically remotely operated. But it can be secured with a proper deployment of all the remote operations using protocols, which would include robust cyber security. Shortcutting cybersecurity measures puts a facility at risk,” says Doetzl.
For wind-farm owners and operators, he suggests that: “A lot of guidance is available from the Department of Energy, National Institute of Standards and Technology (NIST), and NERC regarding properly securing systems. So start with basics. Ask: Is all remote access secured? Use encryption and secure authentication so that anyone accessing these systems must do so in a secure manner. Include security monitoring and incident response. So if something does happen, it is possible to respond quickly and prevent the incident from spreading,” he says.

Radiflow SCADA IDS (Intrusion Detection System) is server-based software that is said to analyze the OT network traffic to protect against cyber threats. The IDS system combines two distinct competences: SCADA/ICS modeling and Anomaly detection. The IDS receives a parallel (mirrored) stream of all network traffic and analyzes it to generate and display a network topology model, and serve as a baseline for detecting exceptions indicating unauthorized traffic. The IDS has six detection engines to cover network visibility, maintenance management, signature-based detections, virtual firewall, anomaly detection, and measuring operational behavior.
Compliance to cyber security standards can be difficult. “I’d say, pick the most appropriate guidance and implement it. If you are subject to NERC compliance, then do that. If not, pick some of the more general guidance around the NIST framework. A lot sounds like eat right and exercise. It’s easy to say but difficult to do. But somebody has to manage these things and keep on top of them,” says Doetzl.
More Doetzl advice: Make sure you have patch management in place to minimize security vulnerability on a regular basis.
As head of cyber security for ABB Enterprise Software, Doetzl says his company’s interest is in making sure it offers secure products,solutions, and services. “We must have secure development practices that ensure our products and services are as free of defects as possible when they get to the customer environment. We make sure our products are secure when delivered and then maintain the security over the lifecycle of the product through services and support.
ICS-CERT, cyber cop
The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), a section of the Department of Homeland Security, is tasked with providing a controls-systems-security focus as part of the national Cybersecurity and Communications Integration Center (NCCIC). The Team’s literature says it provides analyses of vulnerabilities and malware threats to control system environments and it offers asset owners onsite assistance and remote analysis to support discovery, forensics analysis, and recovery effort.

German security analyst and hacker Maxim Rupp, as reported by ICS-CERT, was able to penetrate several poorly designed turbine controls. The Grid Tie screen-grab he captured, from a RLE Nova 6-kW wind turbine, shows that just one selection could cause trouble for the owner. The wind-farm hazard may seem low because ICS-CERT lists only two other turbines as security risks: the U.S. made Xzeres 442SR, a 12.2 kW unit for residential applications, and the Nordex NC (Nordex Control) 2. The ICS-CERT Alert from 2013 is here: http://goo.gl/2VyjYQ
If there is good news, ISC-CERT reports that it and German security researcher Maxim Roop found only three wind turbines vulnerable to cyber-attack and those were small (6 to 12-kW) non-commercial units. Still, ICS-CERT makes these basic recommendations:
• Connect no industrial control system directly to the Internet.
• Place all control-system assets behind firewalls, separated from the business network
• Deploy secure remote access methods, such as Virtual Private Networks (VPNs) for remote access
• Remove, disable, or rename any default system accounts (where possible)
• Implement account lockout policies to reduce the risk of brute forcing attempts
• Implementing policies requiring the use of strong passwords.
• Baseline the organizations control networks to understand what the “normal” communication patterns are within their environment.
• Monitor the creation of administrator-level accounts by third-party vendors (ICSA-10-228-01).
For more on what the ICS-CERT has to say, go here: https://goo.gl/r9zZRR. Or, to report intrusions call (877) 776-7585
SCADA security for the power grid
Bernhard Schuiki / Industry Specialist Energy / COPA-DATA, www.copadata.com
A security engineer turned hacker and cyber-vigilante is one of the most unlikely heroes of this year’s TV summer season. “Mr. Robot” depicts the hacker lifestyle as more than just a parallel universe of today’s society. It has long since become a recurring theme in mainstream culture – no matter how different these depictions happen to be – as well as a steady threat, a constant headline fixture. Just consider the Sony hack in connection with the motion picture “The Interview”, which might or might not have been sponsored by North Korean authorities. More recently, affair-promoting dating portal AshleyMadison.com experienced a massive data breach, releasing gigabytes worth of personal information.
There is, however, a more serious threat that gets insufficient media attention and it pertains to renewable energy systems. The risk of hacked power lines, as experts and recent studies have concluded, could be another danger with unforeseen – and unprecedented – consequences.
The threat for wind farms
COPA-DATA provides holistic cyber security and SCADA solutions for industry 4.0 and the Internet of Things.
In mid-June, reports of Trojan malware spreading through the German Parliament (Bundestag) surfaced with an invitation for a conference containing phishing software, leading to stolen data from at least five computers. If the Bundestag, with its high-grade security system, is subject to data breach, what about other entities, such as energy suppliers?
German security researcher, Maxim Rupp, found several potentially critical flaws in current security systems of solar lighting systems and wind turbines that could be maliciously exploited. In one case, a hacker could have gained complete administrative access of the turbine and possibly “change the wind vane direction, or change the network settings to access the web interface that would make it inaccessible.” This security issue was given the highest vulnerability score due to the mere ease of exploitation.
Lloyd’s of London evaluates the threat of power-plant sabotage by hacking as “improbable, but not impossible.” Yet there is an energy doomsday scenario mentioning years of work implanting malware into power plant control systems all across the U.S. In case of activation, this could lead to the overload and burn-out of several plants across the country, with a potential cost ranging from approximately $250 billion to nearly $1 trillion.
How big a target are wind farms?
In a recent AWEA blog, David Ward showed that American wind plants use up-to-date, sophisticated security methods. As in most other power plants, wind plants use SCADA (supervisory control and data acquisition) systems. Power conversion in turbines provides an additional buffer or firewall between the generator and the power system. As an additional incentive, wind and power plants have commercial reasons for protecting their systems: nobody wants to see their strategies fall into the competitor’s hands. Ward believes that hackers consider wind plants too small to target, but with renewable energy constantly increasing its market share and therefore gaining importance, isn’t this bound to change soon?
Security software developer Klockwork Inc. provides a different outlook and has found a common, remotely exploitable flaw in a certain wind-turbine software. Software development information is publicly searchable and, technically, open to everyone. Having a solution developed and in place can take a lot of time, and it might not even be the permanent answer – a problem certainly not exclusive to the software in question. There are also reports of system updates targeted by hackers in various branches of business. Why not in wind farms, too?
Red Tiger Security conducts penetrating testing and vulnerability assessments on production control systems. The company’s Jonathan Pollet believes that SCADA security matters greatly and perceives its users as the main risk. He believes that, more often than not, engineers and system integrators lack sufficient skills to implement and maintain security in their SCADA systems. This makes the bridge between the company network and HMI network extremely vulnerable. According to a Red Tiger SCADA vulnerability study, it comes as no surprise that the average time from discovering to publicizing flaws and security breaches is a much-too-long 331 days, with the worst case exceeding three years. Certainly, cyber security warnings and issues are everything but a one-and-done issue.
Areas most at risk
Which areas are particularly at risk of hacking threats? With renewable energy continuously on the rise, HVDC (High Voltage Direct Current) power lines could become the “umbilical cords” of energy transfer. With a loss of only 3% per 1,000 kilometers, HVDC lines, in the future, could bring solar energy from the Sahara desert to Europe, but are also becoming more widely used for power plants all around the world, including wind farms. Naturally, they must be extremely well-monitored. SCADA systems are currently employed to ensure the safety of these near-lossless power lines, but they aren’t enough.
Directly hacking these power lines might not really be the issue, yet the danger lies in software bugs and flaws left wide open with little to no security measures.
Attacks could bring HVDC lines down, leading to one of Lloyd’s of London’s energy doomsday scenarios, namely severe loss of power to large metropolitan areas. These attacks could also go in another even more punishing direction. Hackers might be able to reconfigure the entire energy gain system and program turbine reversals. Doing so would not just harm the system, but it could even damage or destroy the wind farms by merely changing the direction in which the turbines revolve. The result: weeks and months of power cuts, plus millions and billions of dollars in repair costs.
Increasing and maintaining security
SCADA security matters greatly, even though it might not always be enough and must be supported by additional security measures and security experts. In addition, SCADA engineers should regularly monitor, update, and re-protect the system from potential threats. Furthermore, it is key to run regular checks to find, identify, and eliminate potential flaws. A Department of Energy report assessed the weaknesses of current industrial control systems for cyber-security and found a great number of devastating bugs and grave errors throughout countless different industry branches. The DOE concluded with a number of basic security recommendations.
Among the most basic recommendations was the creation of a security culture. Reports from Red Tiger Security’s Pollet have shown that a shockingly great number of “regular” SCADA administrators everyday use default, generic, and surprisingly easy passwords to protect increasingly flawed systems. Network protocols must be redesigned for security criterion before it is possible to implement and test further measures, such as highly advanced encryption mechanisms and strong authentications. Storing data in binary code and eliminating SQL servers while the program is running are equally vital, as is the separation of application from engineering.
It’s time to act
If the preventive measures seem impossible to implement, consider assistance from skilled security officers familiar with such measure and other methods. The time to act – and to hire – is now. While some experts believe that wind energy has yet to become an important enough target for cyber-terrorists, you cannot be sure whether or not the seed for an even bigger threat has already been planted and should be removed, ideally three weeks ago. Even if hacking threats are yet to reach wind farms, it is better to be safe than sorry. As your mother so rightfully advised: a stitch in time saves nine.
Shodan find computers
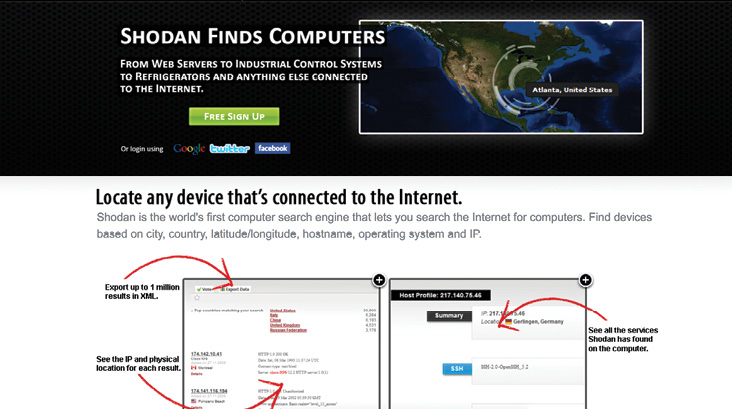
Shodan finds computers, says the Shodan website (shodanhq.com), to expose online devices such as webcams, routers, power plants, and….wind turbines. Even ICS-CERT recognizes the capability of the website and cautions that if Shodan can find your computers, bad guys can too.
That’s not just a headline. It’s the tagline for a search engine that finds Internet facing devices, according to U.S. cyber cop ICS-CERT. The Department of Homeland Security cyber security says, almost as if writing ad copy for Shodan, that its “database contain devices identified by scanning the Internet for the port typically associated with HTTP, FTP, SSH, and Telent. Searches can be filtered by port, hostname, and/or country. FTP and Telnet service banner and client or server messages exchanged during long attempts, and SSH banners (including sever versions).”
One function, says site developer Patrick Stave, (@patstave on Twitter) is to pinpoint shoddy industrial controls. Others, however, say it lowers the technical bar needed to canvas the internet, and it is the Google for hackers.
Filed Under: Uncategorized