Yiwei Chen / Product Manager / Moxa
It is inevitable that the adoption of the Industrial IoT (IIoT) is going to continue to grow, facilitating more and more devices to be connected to networks. The momentum driving this trend is a strong desire from asset owners to enhance operational efficiency. However, achieving enhanced operational efficiency is not without problems. It is forcing asset owners to start to give serious consideration to the dangers posed by cybersecurity threats. Every device that is added to a network creates a potential weak point or vulnerability by providing attackers with a possible entry point to the network. The importance that companies and even governments are starting to place on cybersecurity is hard to overestimate.
 In July 2016, the European Parliament published guidelines that should be adhered to prevent cyber attacks. Asset owners are united in their demands for cybersecurity solutions that allow them to deploy secure devices and networks for industrial applications.
In July 2016, the European Parliament published guidelines that should be adhered to prevent cyber attacks. Asset owners are united in their demands for cybersecurity solutions that allow them to deploy secure devices and networks for industrial applications.
What is the IEC 62443 Standard?
The IEC 62443 standard is constantly evolving to provide up-to-date security guidelines and a list of best practices for different parts of a network. It also includes information for those who perform different responsibilities on the network in order to protect against known security leaks and unknown attacks. The ultimate goal of the standard is to help improve the safety of networks and enhance industrial automation and control settings security.
At present, many system integrators (SIs) require component suppliers to comply with the IEC 62443-4-2 subsection of the IEC 62443 standard that specifically pertains to the security of end devices. The subsection is compiled from foundational requirements, including identification and authentication control, use control, data integrity and confidentiality, as well as backup for resource availability.
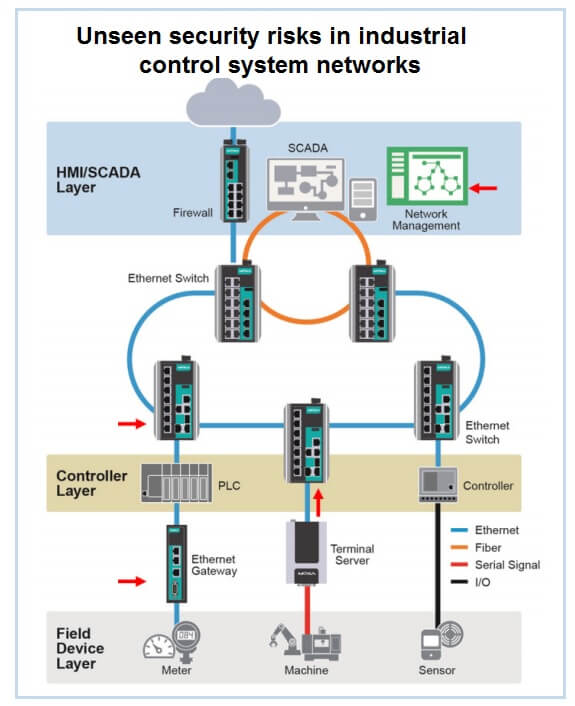
Understanding security risks
The general consensus among security experts is that any of six main cybersecurity threats that can affect internal networks, including unauthorized access, unsecure data transmission, unencrypted key data, incomplete event logs, lack of security monitoring, and human setting errors. It is paramount that network operators understand these threats so that they can deploy devices that have sufficient security features in place and ensure that their networks are safe from internal and external threats.
Consideration will now be given to situations where these security risks can arise and some of the options that are available to network operators in order to neutralize threats to their networks.
Register and read the rest at: https://goo.gl/SEO3zl
Filed Under: Cybersecurity




